Key Differences between Security Groups and Network Access Control Lists (NACLs) in AWS
AWS Series (Part-5)
Table of contents
Introduction
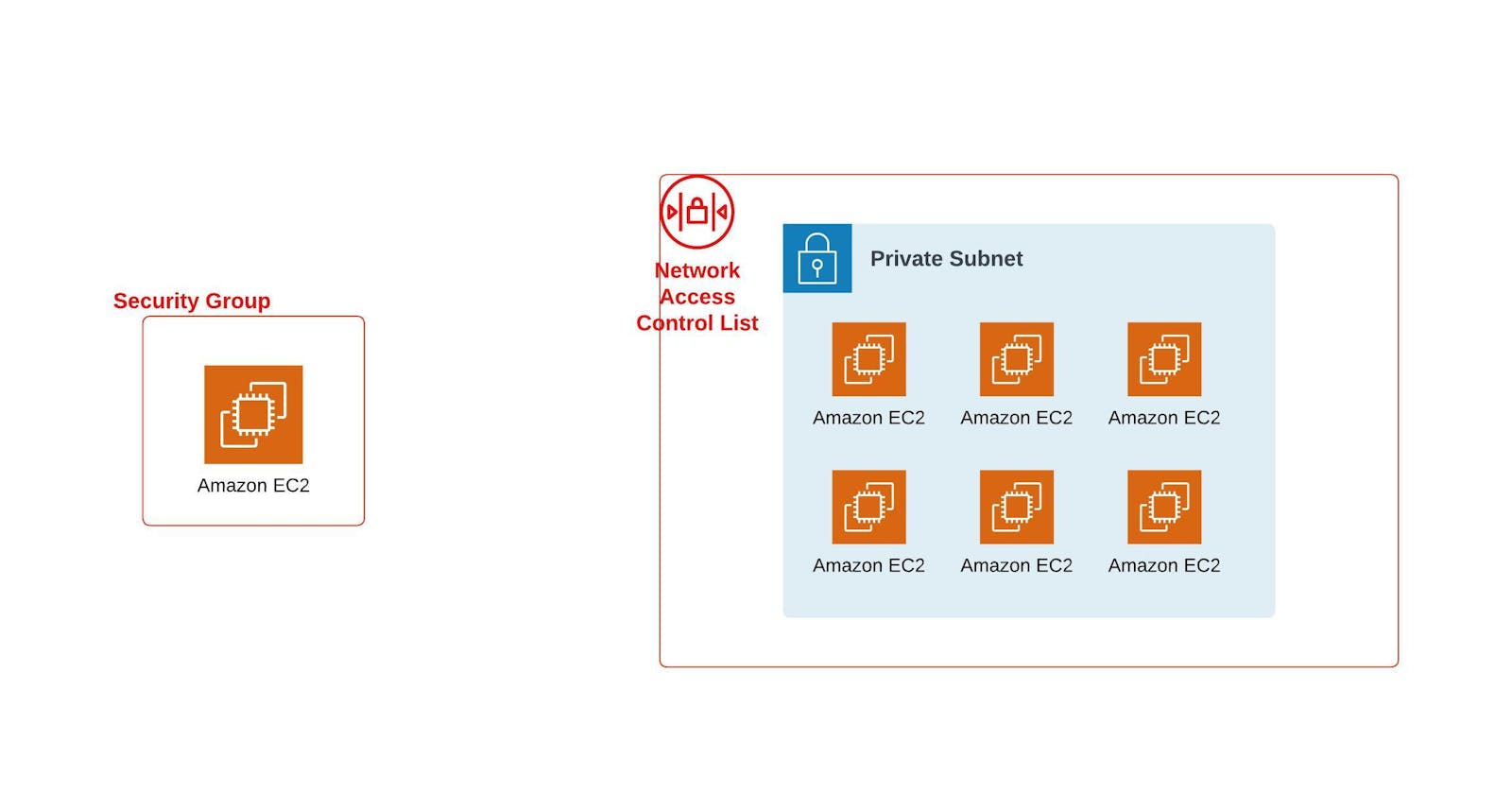
Security Groups: A security group in Amazon Web Services (AWS) serves as a virtual firewall for your Amazon Elastic Compute Cloud (EC2) instances and is a basic component of network security. Using rules you define, security groups manage traffic both coming into and going out of your EC2 instances and other AWS resources, like Amazon RDS databases.
Network Access Control Lists (NACLs): Network Access Control Lists (NACLs), in addition to security groups, are a crucial part of network security in Amazon Web Services (AWS). Stateless network security structures called NACLs function as a firewall to regulate traffic entering and leaving Amazon Virtual Private Cloud (VPC) subnets. NACLs function at the subnet level, whereas security groups function at the instance level.
Key Differences
Stateful vs Stateless:
Security groups are stateful, allowing inbound traffic from a given IP address also automatically permits outbound traffic to that same IP address. This makes maintaining security rules easier.
NACLs are stateless in contrast to security groups, which are stateful. This implies that for every unique traffic pattern, you have to specify different inbound and outbound rules. In other words, you have to explicitly allow the outgoing response traffic to return if you allow incoming traffic from a given IP address and port.
Rule Evaluation:
In security groups, the most specific rule that matches the traffic is given priority when rules are compared in a particular order. Traffic is allowed if there is an "Allow" rule allowing it. By default, traffic is denied if no rule matches.
NACL rules are assigned numerical rule numbers. Lower-numbered rules are given priority when evaluating rules, and this order is determined by these numbers. If no other rules match, the default rule, 100, is used.
Default Behavior:
With security groups, all outgoing traffic is permitted and all incoming traffic is by default denied. To clearly allow traffic, you make rules.
With NACLs, all incoming and outgoing traffic is permitted by default. To expressly allow or deny traffic, you create rules.
Rule Criteria:
In security groups, port ranges, protocols, and source/destination IP addresses serve as the foundation for rules. With these criteria in mind, you create rules that allow or deny traffic.
Just like security groups, in NACLs, rules are based on source and destination IP addresses, port ranges, and protocols. These criteria are used to define rules that allow or deny traffic.
Association:
Security groups are associated with specific EC2 instances. A single instance may be connected to more than one security group.
NACLs are associated with VPC subnets. Only one NACL can be connected to each subnet.
Conclusion
To summarize, stateful rules are used by security groups; they make rule management easier and are more restrictive by default. NACLs employ stateless rules, which are permissive by default and call for specific inbound and outbound rules for every traffic pattern. While security group rules are assessed according to their specificity, NACL rules are ranked according to explicit rule numbers. You can achieve the appropriate degree of control and security for your resources when configuring network security in AWS by combining security groups and NACLs.