In this project, we will use AWS Fargate to facilitate serverless container execution while orchestrating the deployment of an Amazon EKS (Elastic Kubernetes Service) cluster. Using the AWS Load Balancer Controller, we will also deploy an application with an Application Load Balancer (ALB). The goal of this project is to demonstrate mastery of Kubernetes and related services for cloud-native application deployment on Amazon Web Services.
Prerequisites:
- Install kubectl
- Install eksctl
- Install and configure AWS CLI
Steps:
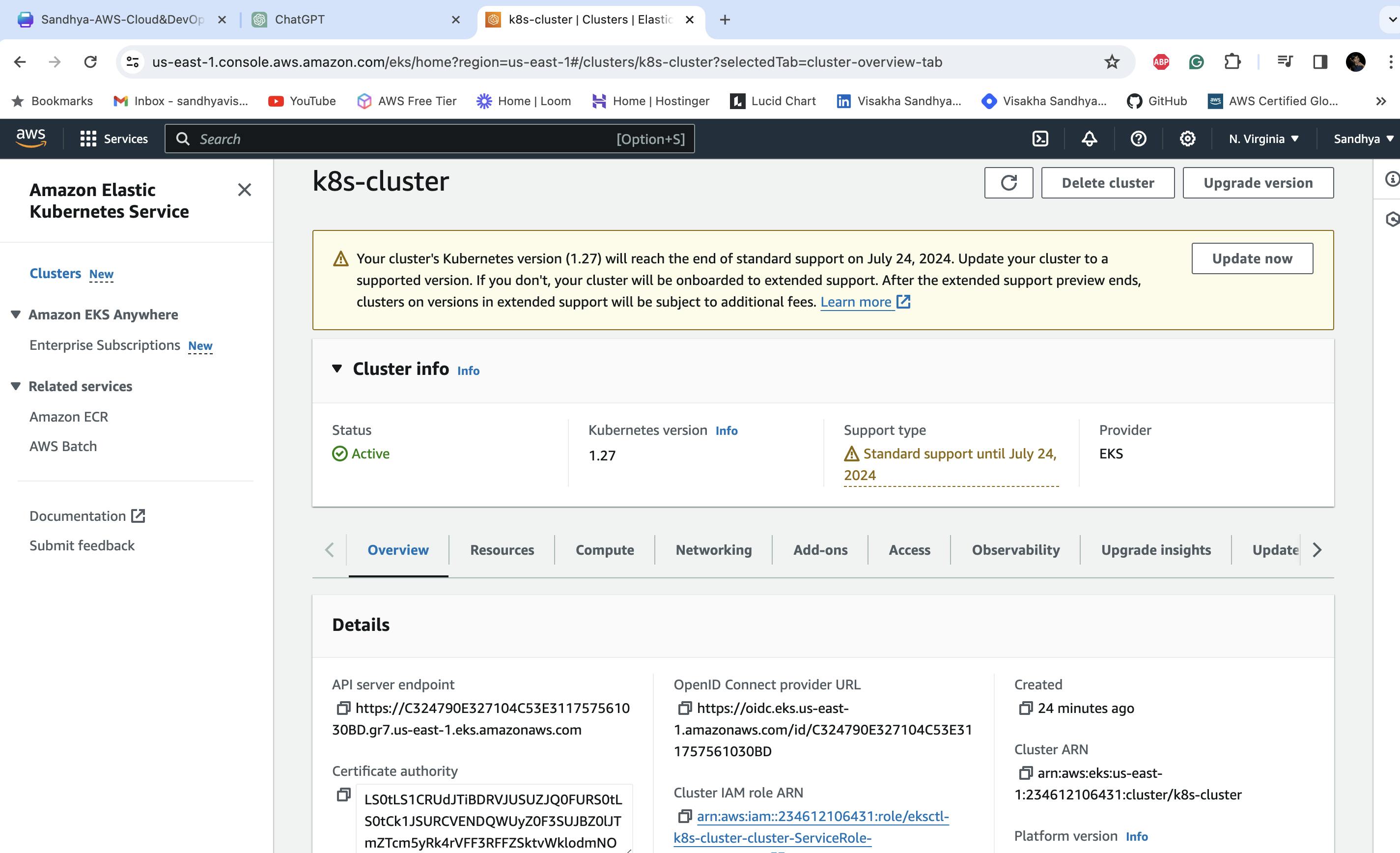
1. Create an Amazon EKS cluster named k8s-cluster in the us-east-1 region using eksctl.
eksctl create cluster --name k8s-cluster --region us-east-1 --fargate

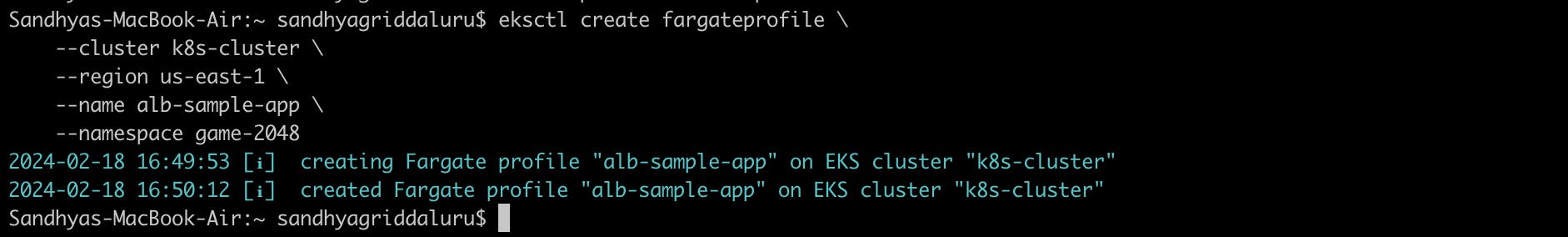
2. Configure a Fargate profile named alb-sample-app for the namespace game-2048.
eksctl create fargateprofile \
--cluster k8s-cluster \
--region us-east-1 \
--name alb-sample-app \
--namespace game-2048
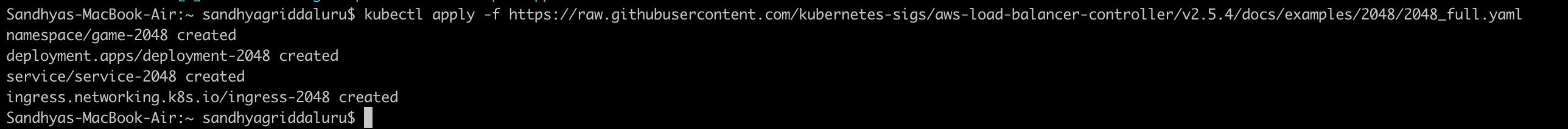
3. Deploy a sample application (which in this case is 2048 game) onto the EKS cluster using Kubernetes manifests.
kubectl apply -f https://raw.githubusercontent.com/kubernetes-sigs/aws-load-balancer-controller/v2.5.4/docs/examples/2048/2048_full.yaml
4. To enable IAM roles for service accounts, associate the EKS cluster with an OIDC provider.
eksctl utils associate-iam-oidc-provider --cluster k8s-cluster --approve

5. To grant the required permissions for the AWS Load Balancer Controller, create an IAM policy called AWSLoadBalancerControllerIAMPolicy.
curl -O https://raw.githubusercontent.com/kubernetes-sigs/aws-load-balancer-controller/v2.5.4/docs/install/iam_policy.json
aws iam create-policy \
--policy-name AWSLoadBalancerControllerIAMPolicy \
--policy-document file://iam_policy.json
6. In the kube-system namespace, create an IAM role called AmazonEKSLoadBalancerControllerRole and associate it with the aws-load-balancer-controller service account. To grant permissions, attach the AWSLoadBalancerControllerIAMPolicy to the IAM role.
eksctl create iamserviceaccount \
--cluster=k8s-cluster \
--namespace=kube-system \
--name=aws-load-balancer-controller \
--role-name=AmazonEKSLoadBalancerControllerRole \
--attach-policy-arn=arn:aws:iam::<your-aws-account-id>:policy/AWSLoadBalancerControllerIAMPolicy \
--approve

7. Update and add the EKS Helm chart repository. Next, install the AWS Load Balancer Controller Helm chart in the kube-system namespace and set up the cluster name, region, VPC ID, and service account settings.
helm repo add eks https://aws.github.io/eks-charts
helm repo update
helm install aws-load-balancer-controller eks/aws-load-balancer-controller \
-n kube-system \
--set clusterName=k8s-cluster \
--set serviceAccount.create=false \
--set serviceAccount.name=aws-load-balancer-controller \
--set region=us-east-1 \
--set vpcId=<your-vpc-id>
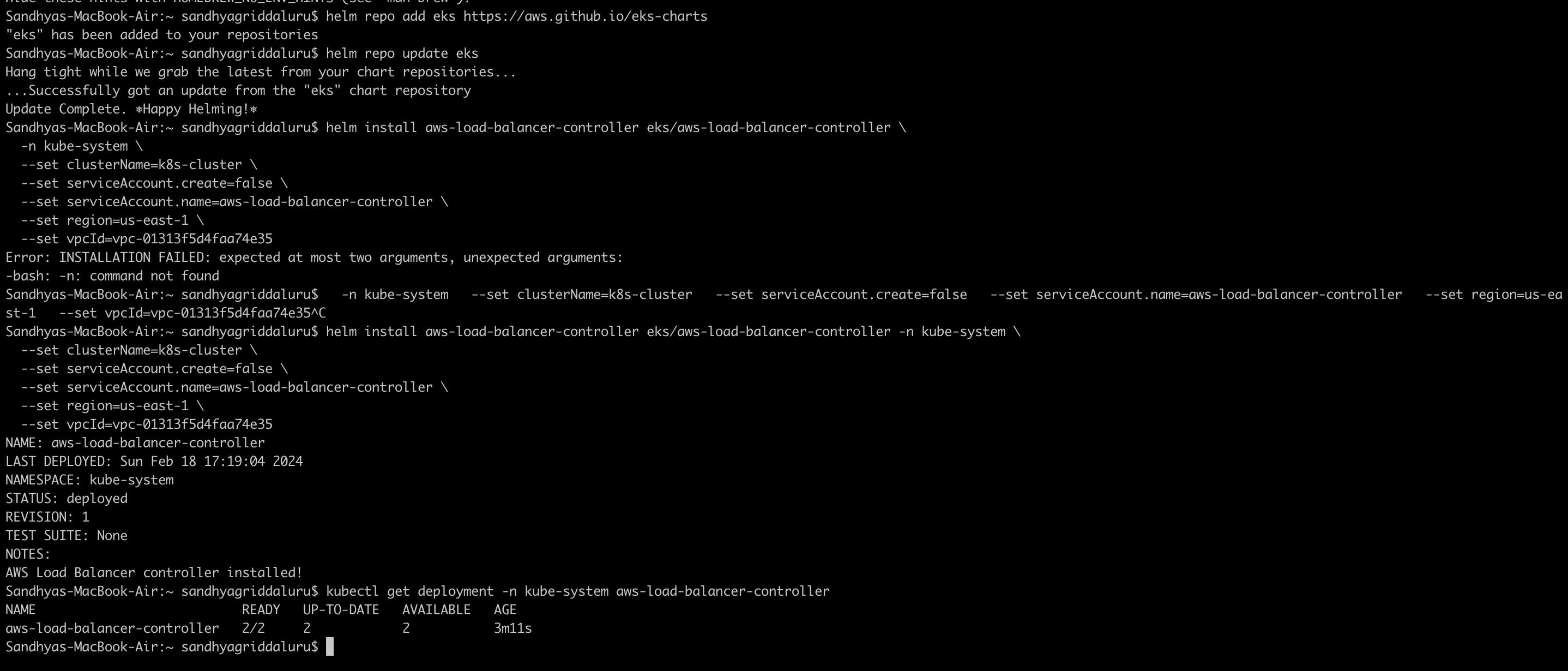
8. To confirm a successful installation, check the AWS Load Balancer Controller's deployment status using
kubectl get deployment -n kube-system aws-load-balancer-controller
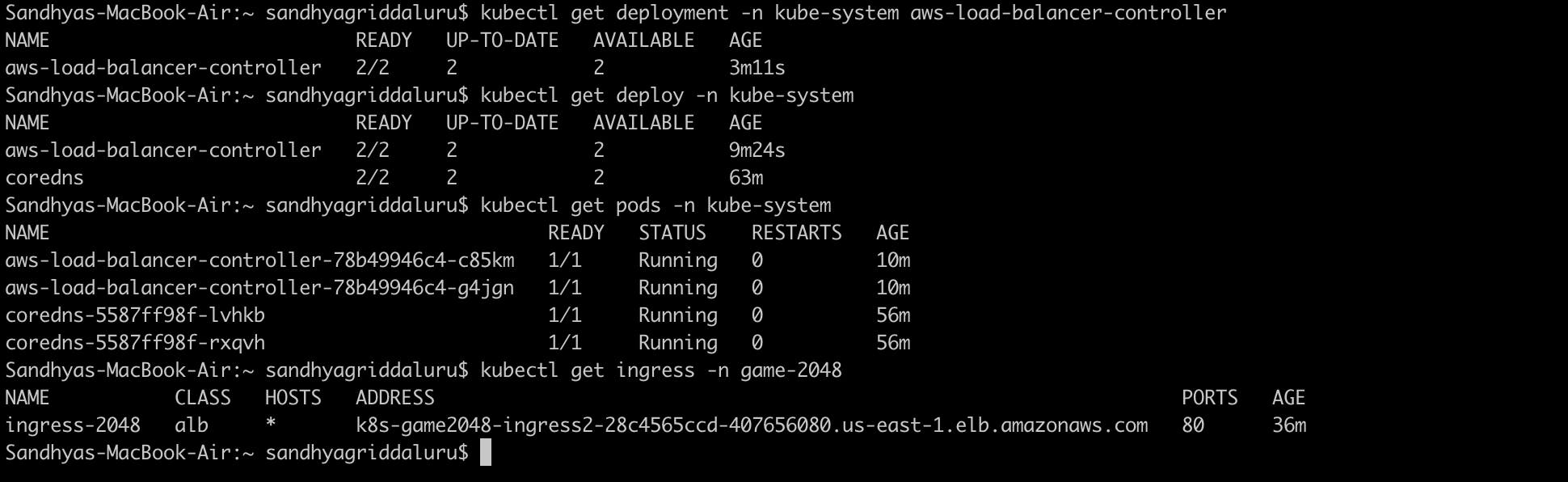
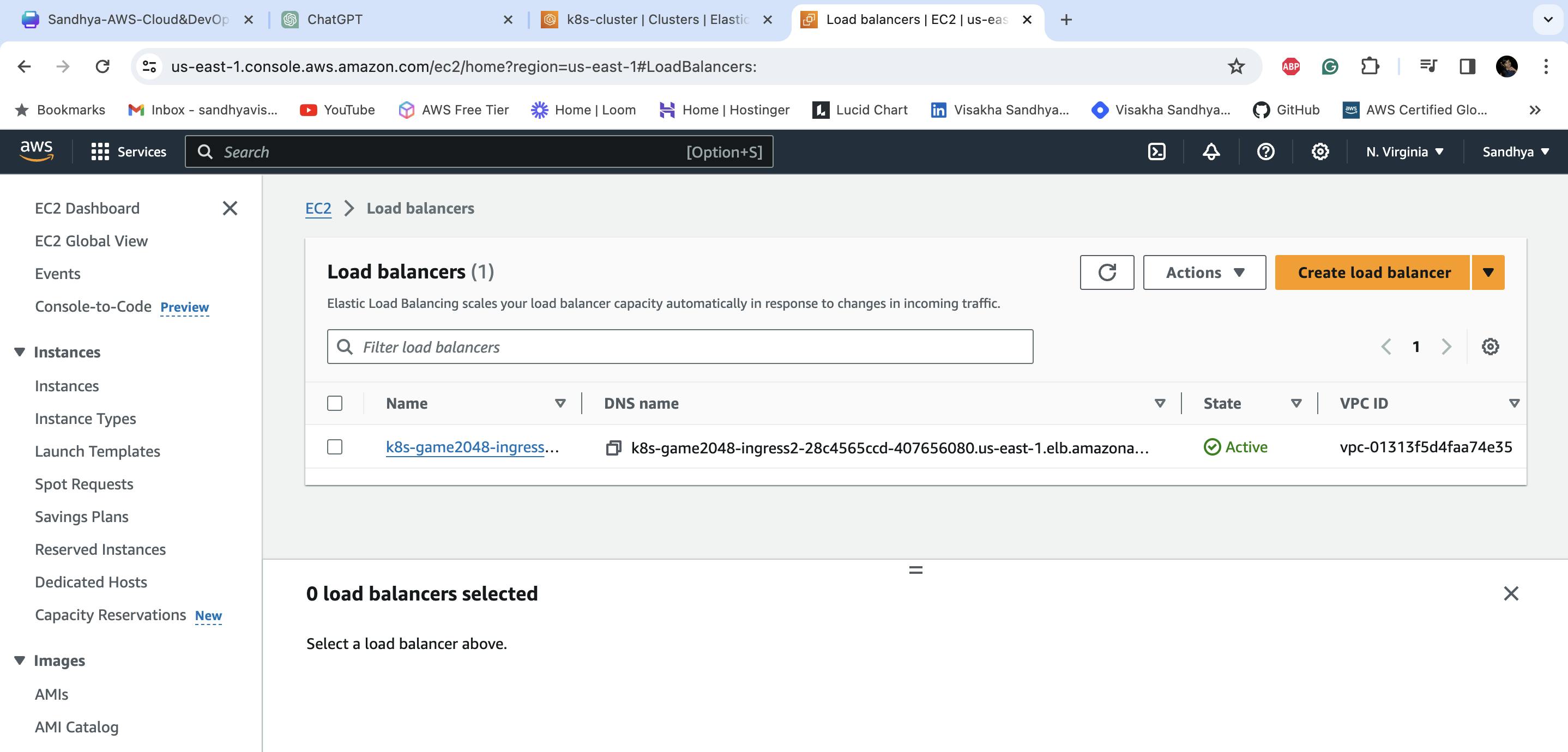
9. Now, verify that the application is accessible using the application load balancer ingress ID.
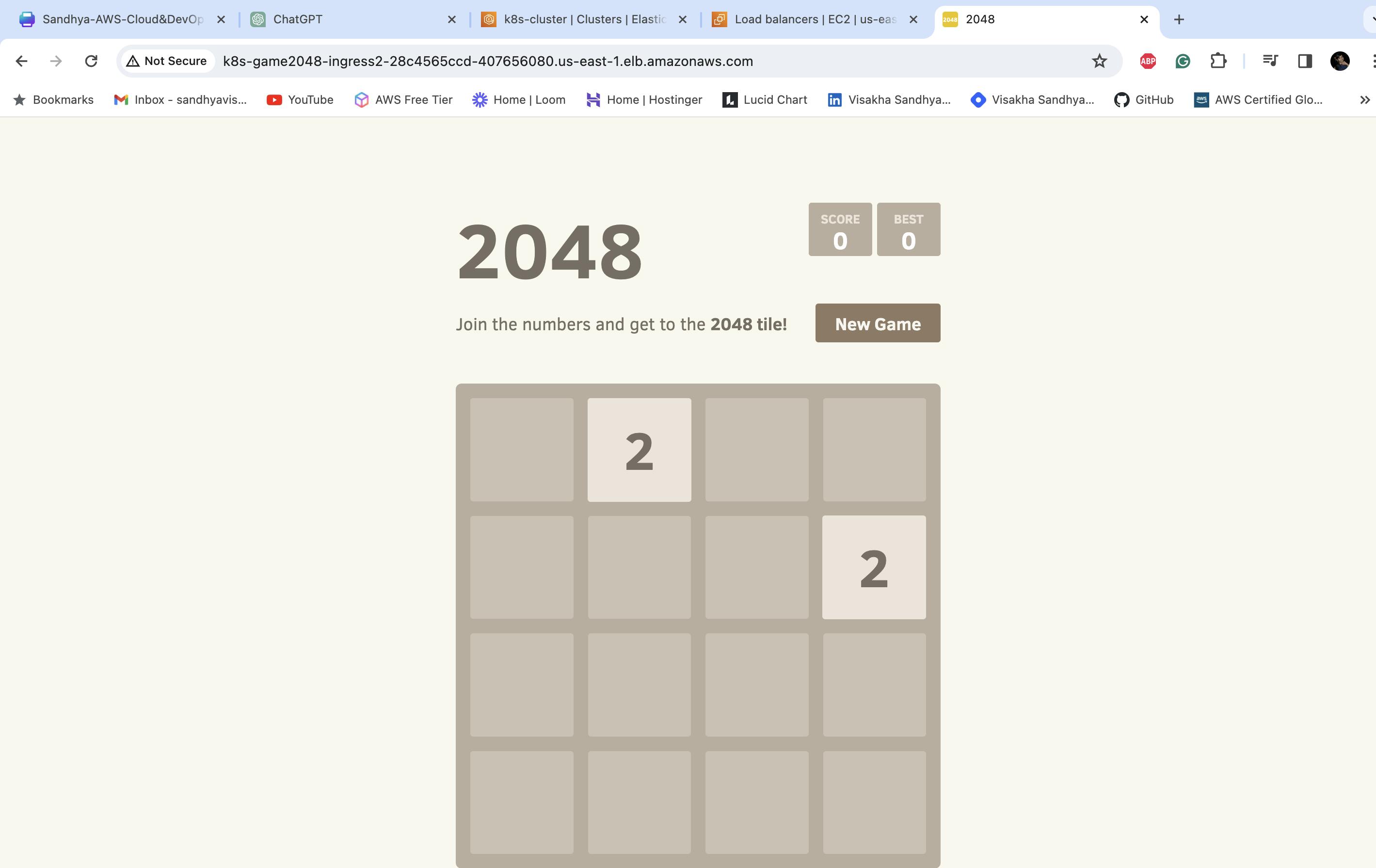
Successfully integrated AWS Load Balancer Controller for ALB provisioning, deployed a sample application, and set up an Amazon EKS cluster with Fargate. For the purpose of deploying scalable and resilient applications, this project showcased expertise in cloud infrastructure provisioning, Kubernetes orchestration, and AWS service integration.